Software Risk Management Program
Review BEFORE you buy.
Buying or using new software at UMD? Start here.
Before purchasing or using new software at the University of Maryland, you’ll need to determine which review path applies to your request. Depending on cost and how the software will be used, your request may follow either:
- the Software Risk Management (SRM) review process, or
- an expedited procurement path for lower-risk software.
Use the guide below to determine the right next step.
Two ways software requests are reviewed at UMD
Option A: SRM Review
SRM is the standard review process for software that may involve security, privacy, or accessibility risks or that will be used broadly across the university.
The SRM process includes reviews by IT Compliance, Data Privacy, and Accessibility teams before procurement. This process does not assess terms and conditions, which are handled by the Department of Procurement and Business Services before an agreement is signed or a purchase is completed.
Option B: Expedited Procurement
Expedited procurement is a faster path for lower-risk software that meets specific criteria related to cost and use.
Not all software is eligible for expedited procurement.
Option A: Software Risk Management
Software Risk Management is the University of Maryland’s process for reviewing third-party software and applications before they are purchased or used. SRM helps ensure that software meets the university’s requirements for security, privacy, accessibility, and regulatory compliance, and that risks are identified and addressed before procurement.
This process includes coordinated reviews by:
- IT Compliance (security),
- Data Privacy, and
- Accessibility.
Option B: Expedited Procurement
The expedited process allows departments to acquire lower-risk software licenses more quickly - bypassing the full Software Risk Management review - if specific criteria related to cost and use are met.
Not all software is eligible for expedited procurement.
How do I know which path applies to my request?
Use the questions below to determine whether your software qualifies for expedited procurement or requires SRM review.
If you answer “Yes” to any of the following questions about sensitive data, instructional use or cost, your request requires SRM review:
- Will the software store/process restricted or sensitive data?
- Will the software be used for instruction or core academic activities?
- Is the cost over $25,000?
More information about the SRM process is provided on this site below.
If you answer “No” to the above questions, you may use the expedited procurement process.
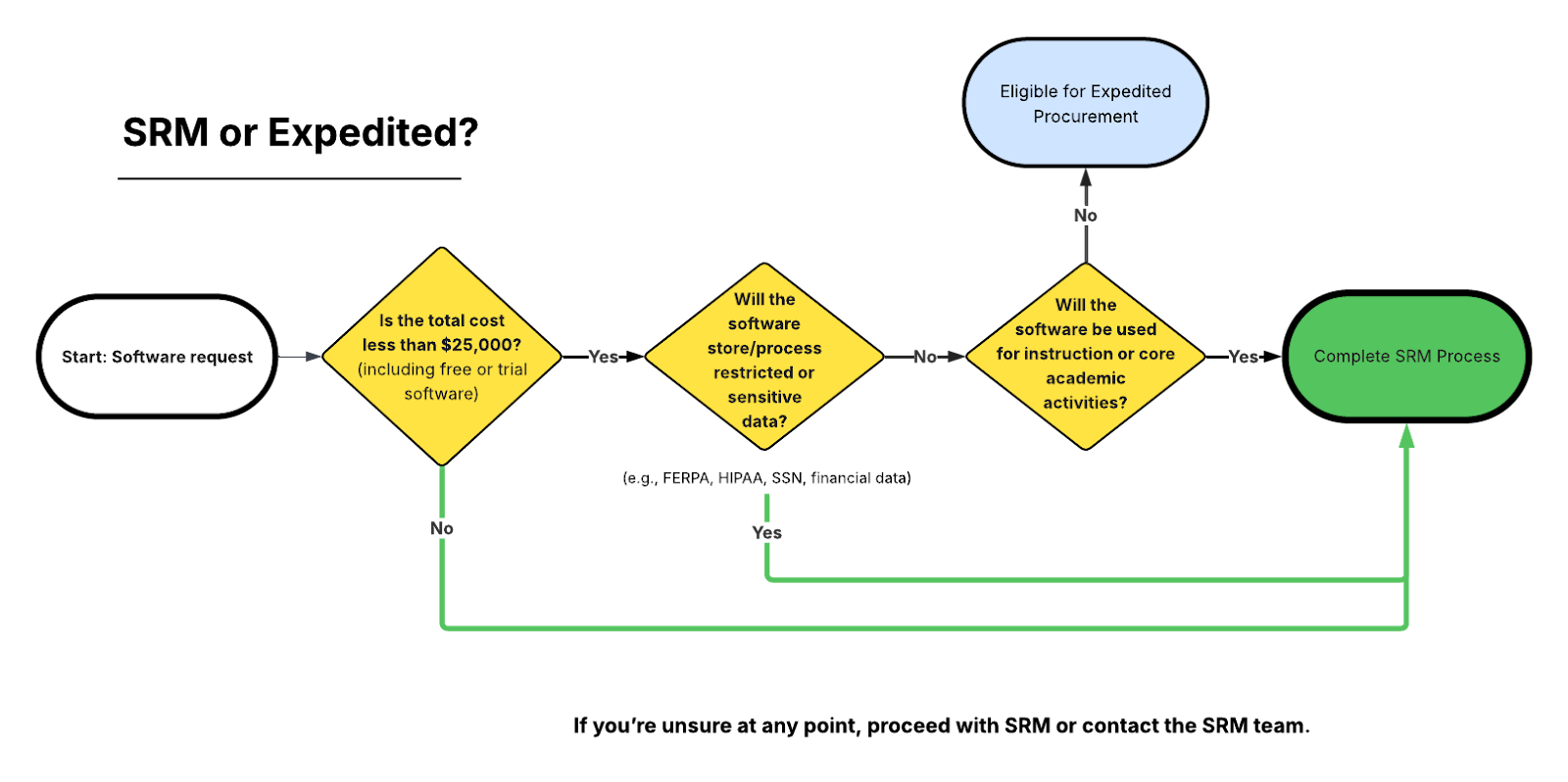
Not sure which path applies?
If you’re uncertain about data sensitivity, instructional use, or eligibility, proceed with SRM or contact the SRM team at software-risk-mgmt@umd.edu for guidance.
Expedited Procurement
Your request may proceed using expedited procurement only if ALL of the following are true:
- The total cost is less than $25,000 (including open source, free, or trial versions).
- The software does not store or process restricted or sensitive data.
- The software is not used for instruction, coursework, or required academic activities.
Proceed with expedited procurement by submitting the Expedited Procurement Form. If you have further questions about the Expedited Procurement Process please reach out to SPARCS@umd.edu.
SRM Purpose
All software, software as a service products, and cloud acquisitions must complete the Software Risk Management (SRM) assessment before purchase. This process ensures that:
- Security risks are identified and mitigated.
- Data privacy concerns are addressed.
- Digital accessibility requirements are met.
- Contracts are reviewed for compliance and risk exposure.
- Solutions are compatible with UMD’s IT infrastructure.
The SRM Program aims to:
- Protect UMD's Interests: Safeguard the university's data, systems, and reputation by evaluating the security and compliance posture of third-party vendor applications and software.
- Ensure Compliance: Align vendor engagements with applicable laws, including FERPA, HIPAA, and state procurement regulations.
- Promote Efficiency: Streamline the acquisition process to prevent redundancy, reduce service duplication, and ensure compatibility with existing systems.
- Enhance Transparency: Maintain a centralized list of approved applications and software for institutional awareness and oversight.
SRM Review: How to Start
- Initiation: Confirm whether the software is already approved for use and exists on the Software Catalog. If the software is not listed on the Software Catalog, departments identify the need for a new software and send a completed SRM Assessment Form to software-risk-mgmt@umd.edu. Note: Starting March 2, 2026, the SRM process will move to Workday. Requestors will submit SRM requests through a Workday requisition and attach the completed SRM form directly to the requisition, rather than emailing it.
- Risk Evaluation: The SRM team assesses the solution's security, data privacy, and accessibility risk by collaborating with relevant stakeholders, including IT Compliance, IT Accessibility, Data Privacy, and Legal teams for a comprehensive evaluation.
- Approval and Registration: Upon approval, the SRM team will send the requestor an approval form and then the requestor can proceed with the procurement process. Note: Starting March 2, 2026, SRM approval will be captured in Workday. Once software is SRM-approved, the requisition will continue through the procurement process in Workday.
SRM Scope
This process applies to all University of Maryland departments, units, affiliates, faculty, staff, workforce members, and sponsored affiliates who engage in contractual relationships with third-party vendors or contractors for IT applications and/or software. For any software that doesn’t meet the Expedited Procurement Process and is not purchased with a Pcard, the full SRM process will be needed. Examples of when the full SRM process is needed include:
- The tool or service involves an agreement/contract (with or without costs, including a “click-through” agreement where you accept the terms of use) with a service provider who provides a network-accessible service on behalf of UMD to collect, transmit, or process any institutional data.
- The tool or service requires a service provider to process payment card information on behalf of UMD. This includes all entities involved in the payment card process including merchants, processors, issuers and service providers. This also applies to all other entities that store, process, or transmit cardholder data and/or sensitive authentication data. Payment Card processing will be included in the review if the Credit Cards data element is selected.
- The tool or service involves transferring any institutional data from a university-owned system to a third-party system, including cloud and Software as a Service solutions.
- The tool or service requires a third-party system to collect or process any institutional data that will later be transmitted for use by UMD.
- The tool or service is used by students as a part of coursework and collects and/or stores personally identifiable information, including intellectual property or grades.
- The tool or service makes a copy of documents or materials containing any of the data elements described above or that are classified as elevated or high risk according to the UMD Data Classification Standard (IT-2) (i.e., institutional, financial, or student data).
- The tool has not been tested for security vulnerabilities.
Timeline for SRM Reviews
The average duration of each review depends on several factors, including the complexity of the request, the completeness and timeliness of submitted documentation, and the current volume of requests under review. As a general guideline, once requested materials are received from the vendor, departments should plan for approximately 3 to 4 weeks (15–20 business days) once all required documents are received to receive SRM approval or disapproval. Only after the software/tool is approved can the item be procured.
Roles and Responsibilities
- Requestor: Initiate SRM assessments and ensure compliance with the process in a timely manner. Fill out appropriate forms as needed.
- SRM Team: Conduct risk evaluations and coordinate reviews with stakeholders.
- Vendor: Provide requested materials and respond in a timely manner with full cooperation.
- Office of General Counsel (as needed): Review contractual terms and compliance obligations.
- Procurement: Ensure adherence to procurement policies and procedures.
Annual Review
The SRM process will undergo an annual review to incorporate changes in regulatory requirements, emerging risks, and institutional priorities.
To ensure continued protection of university data, all applications and software will undergo a re-review every three years. This regular review cycle enables the university to adapt to evolving security standards and vendor management practices.
Any application or software that is not approved through the SRM process will be eligible for a re-review after 1 calendar year.
Resources
- SRM Assessment Form: SRM Assessment Form
- Software Catalog: University of Maryland Software Catalog
- SRM Office Hours: Every Thursday between 10 and 11 a.m. starting on January 22, 2026 via Zoom
- Software Risk Management Team: The SRM team is the primary point of contact for the Software Risk Management Process. Contact the SRM Team at software-risk-mgmt@umd.edu.
FAQs
Reviews typically take 3-4 weeks once all documents are received. Reviews will be delayed if all documents are not received in a timely manner.
In addition to submitting the SRM Assessment Form, additional documentation may be requested such as:
- Voluntary Product Accessibility Template - The software company is responsible for providing the VPAT.
- System and Organization Controls 2 (SOC2) form - The software company is responsible for providing the SOC2.
Any faculty or staff member may initiate a review.
There are several instances where a new review should be submitted.
- When a new piece of software is being procured
- When the data classification level is being updated
- Certain software will need to be re-reviewed - typically 3 years after the initial review
- Change in use or features
Exceptions are very rare and made on a case-by-case basis. Please reach out to the Software Risk Management Team for exceptions.
Please email the Software Risk Management Team to check on the status of your individual review. Please be sure to include the name of the title being reviewed.
Starting March 2, 2026, requestors can view the status of the SRM request in the requisition process history within Workday.
Please email the Software Risk Management team to edit the information on your review.
Some tools note free use, but when you get to the agreement, terms, or web descriptions, it is disclosed that the tool is free for personal (vs. enterprise) use, for one install/one user only, or that it has other restrictions. Even if it is free, there are still risks that are posed and the software must be reviewed using either SRM or the expedited procurement process (if criteria are met).
There are several individuals and groups involved in the review process:
- Requestor
- Software Risk Management Team
- IT Accessibility Team
- Data Privacy Team
- IT Compliance Team
- Office of General Counsel (as needed)
- Procurement and Business Services
If a vendor signature is required, you must route your agreement through Workday to Procurement and Business Services.
Only Procurement and Business Services has signatory authority. Any agreements requiring a physical signature must be routed through Procurement.
Universities must comply with various federal and state regulations regarding data protection. Risk assessments ensure that third-party providers meet these legal requirements, helping the university avoid penalties, audit findings, legal issues and protecting the university reputation.
Each review group is looking at different aspects of the tool.
- ADA: Compliance with campus and federal ADA guidelines and regulations. Whether or not a tool is required for class or departmental work.
- Data Privacy: How the vendor will store and use university data.
- IT Compliance: Whether the third-party providers meet legal requirements, helping the university avoid penalties, audit findings, legal issues and protecting the university reputation.
Yes. However, any of these titles are subject to future review and, potentially, removal.
